Tetra LabX Agent Frequently Asked Questions
What LabX versions does the Tetra LabX Agent support?
The Tetra LabX Agent supports LabX versions 10 and higher; however, it's recommended that customers use LabX v13 or higher.
The Agent uses LabX SDK APIs (BasicIntegrationService and/or SystemIntegrationService) to fetch data from LabX. In LabX v12 and earlier, METTLER TOLEDO acknowledged that the use of the LabX SDK APIs can lead to an increase in CPU and memory consumption. They have since implemented a fix for this in LabX v13. For optimal performance with the Tetra LabX Agent, it is recommended that customers upgrade to LabX v13.
Why does a LabX server error display when I try to connect the Tetra LabX Agent?
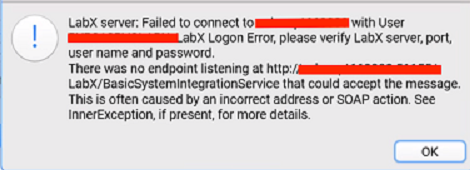
Server Error
To troubleshoot the error:
- Log in to the LabX app server and run the
installation checkerapp (same folder as the actual LabX app). - From the
installation checkerapp, click Run to initiate a system check (this may take a few minutes). - When the check completes, search for the
SystemIntegrationServiceand review the following:- Does the endpoint URL match the one entered in LabX Agent?
- Is the port open on the server?
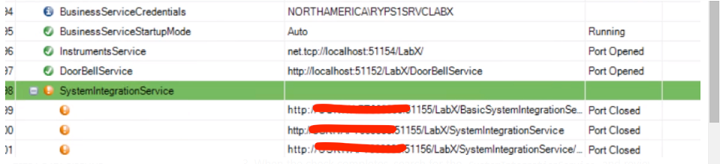
Error Review
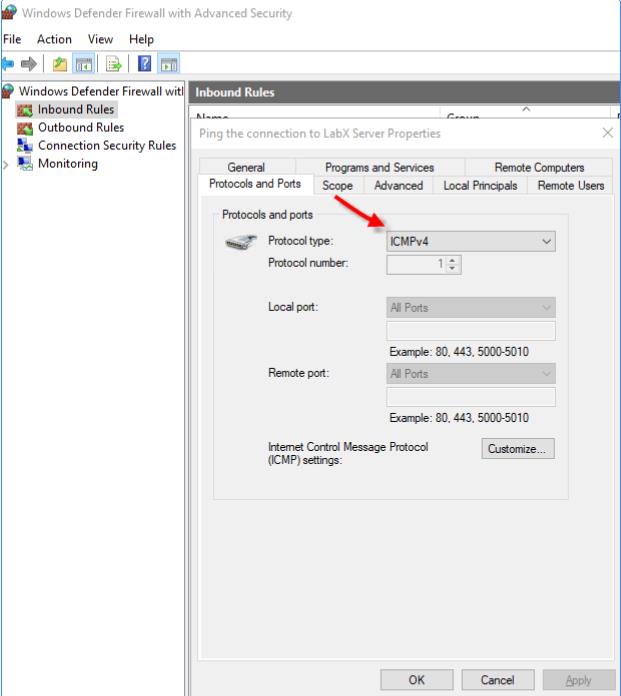
How do I configure LabX Software to allow remote access?
The LabX SDK uses an HTTP API to configure the LabX Agent on a separate virtual machine (VM) from the LabX Software. By default, during a proper installation of LabX, the necessary firewall port exceptions are configured automatically. On the LabX Server machine, you must make sure that the following ports are open:
- Port 51155 for both production and development environments
- Port 51156 for development purposes
You must also create a Firewall Inbound Rule for ICMPv4 from the LabX Software host server.
After installing the Tetra LabX Agent, why doesn't it start when I double-click and instead indicates that "Tetrascience.Agent.LabX.WinApp has stopped working"?
The v1.0.0 Tetra LabX Agent does not include the Admin role requirement in its manifest file. You may need to manually launch the application "as administrator".
Please always run the app 'as administrator' until the next version is released to avoid permission issues
What is the LabX endpoint address that the Tetra LabX Agent communicates with?
The Tetra LabX Agent uses this LabX endpoint address:
http://<address of server>:51155/LabX/BasicSystemIntegrationService
How to configure LabX to integrate over Https
By default, LabX API is not configured for using HTTPS protocol. The LabX client application communicates with the server over a secure channel, only the API by default is not configured for a secure protocol. The procedures below are to make the configuration secure.
Just a reminder that this configuration change is not officially tested and supported by the vendor
- Open the file
C:\Program Files (x86)\METTLER TOLEDO\LabX\LabXHost.exe.configwithin a text editor. Note that in order to save the file after editing, administrative privileges are required. It is recommended to make a copy of the file before editing it. The file is in XML format - File the element
<bindings>and add the HTTPS binding configuration as this example:<bindings> ... <basicHttpsBinding> <binding name="SystemIntegrationBasicHttpsBinding"> </binding> </basicHttpsBinding> ... </bindings> - Find the element
<services>and within this element block find the service with the nameMT.Sequoia.SystemIntegration.SystemIntegrationService, add theBasicHttpsBindingas<endpoint binding="basicHttpsBinding" bindingConfiguration="SystemIntegrationBasicHttpsBinding" contract="MT.Sequoia.SystemIntegration.Contracts.IBasicSystemIntegrationService" address="https://[server name]:51157/LabX/BasicSystemIntegrationService"/> - Note that during an update of LabX, the above-mentioned changes may be underdone by the installation and you would have to verify and eventually redo that change.
- In order for LabX to be allowed by the operating system to use port 51157, permission must be given (http://go.microsoft.com/fwlink/?LinkId=70353)
Note thatLocal Serviceis the account running the LabXHost service. You can check yours to replace this accountnetsh http add urlacl url=https://+:51157/LabX/BasicSystemIntegrationService user="Local Service" - The SSL certificate to be used for HTTPS communication on port 51157 has to be configured. The certificate has to be provided by the customer's IT department.
Note that the IP address 0.0.0.0 must be indicated as such. The App ID provided corresponds to the App ID for LabX. The command to be executed will be similar to this one:netsh http add sslcert ipport=0.0.0.0:51157 certhash=[put certificate hash here] appid={2887C40E-F4F2-4E73-AE77-F85E6FDD3974} - Restart the service LabXHost. If the service doesn't start correctly, you should be able to find a reason in the log file (C:\Program Files (x86)\METTLER TOLEDO\LabX\LogErrorBusinessServerX].txt.txt). If the service starts correctly, you should be able to from SOAP UI (or other tools) to access the LabX API over HTTPS on port 51157.
Which tasks are selected by the Tetra LabX Agent?
The task selection is based on two criteria:
- Task
Creation Dateis later than theTask Creation Datewhich you specify on the Management Console. - Task State. The Tetra LabX Agent excludes all tasks which are still processing. The Task State selection includes these states:
- Completed
- Aborted
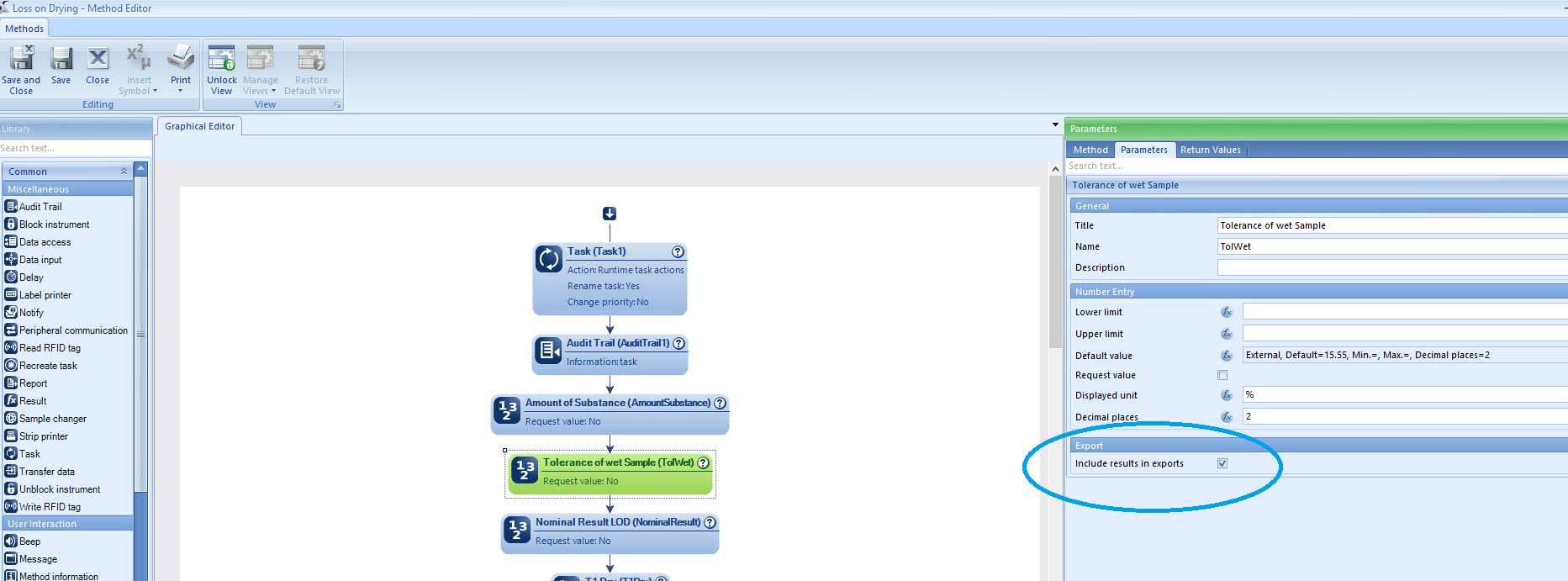
How to export the method parameters?
The parameters of a method can be selected or implemented depending on the application (LabX Operational Manual, Page 190, Section 7.6.3.3 ). A user might change the value of a method parameter during the experiment. The changed value can be exported to the result file if the "include results in exports" checkbox is checked. (see the screenshot below)
How to fix the folder security right error?
After a user clicks on the "Start" button, the service start can be failed with this error message "User XXX has no access to this folder: YYYY". It can be fixed by changing the windows folder security settings.
- Open that folder in the Windows Explorer, right click on the folder and select the "Properties"
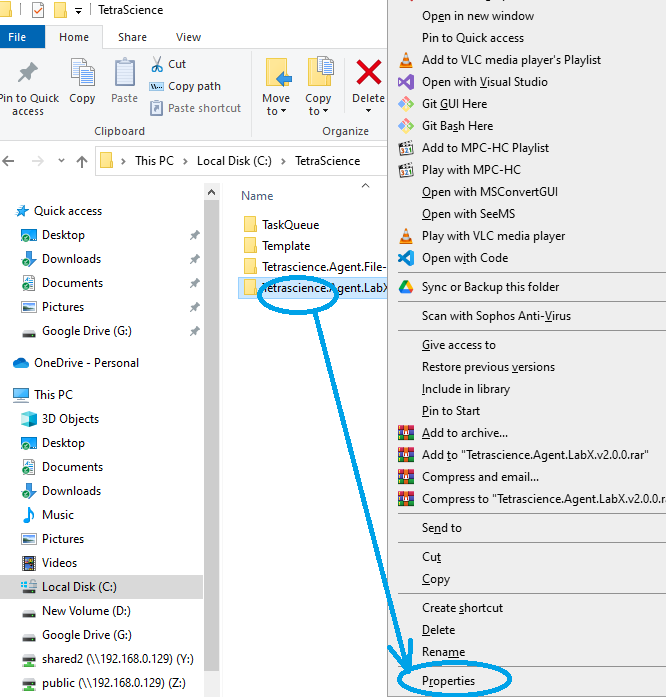
Folder Properties
- Select the "Security" Tab and click on "Advanced"
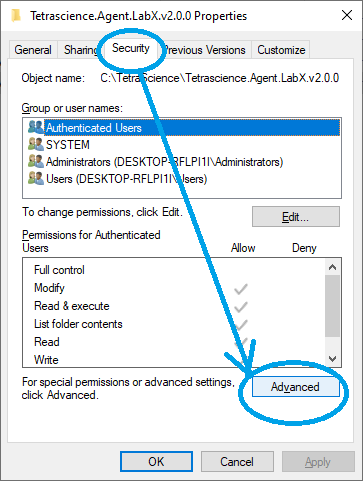
Security Advanced
- Select "Add", then "Select a principal", input user name, click on the "Check Name", click on "OK", then select "Modify" and "Write" access right.
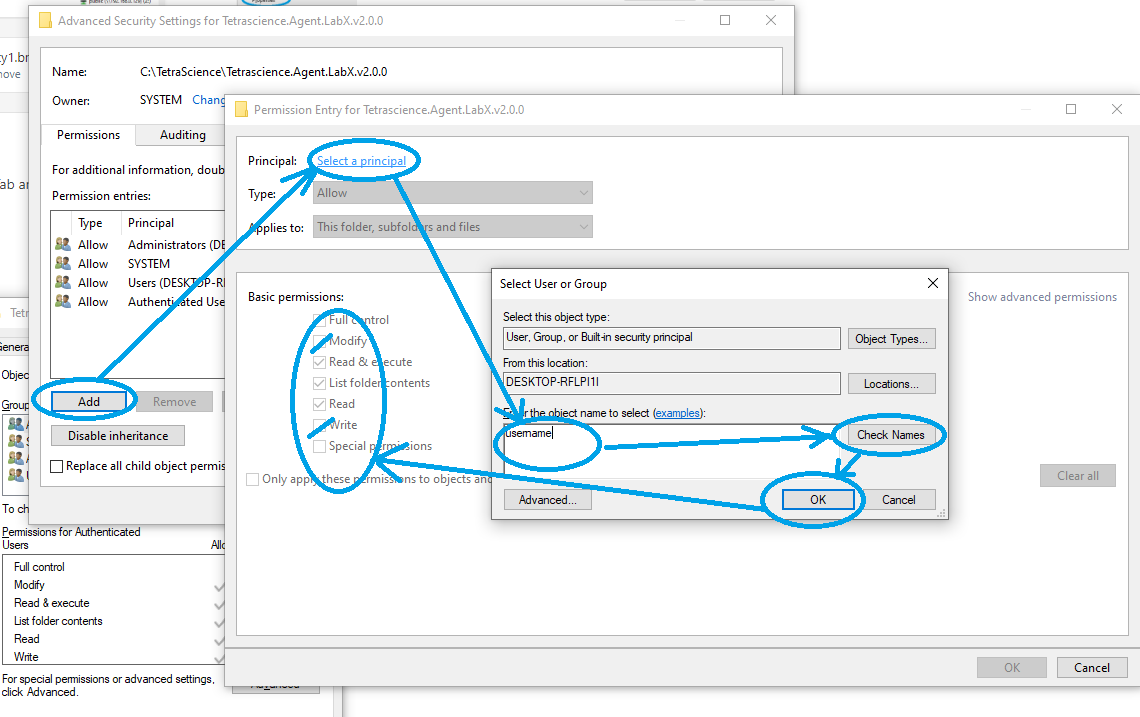
Add user
Documentation Feedback
Do you have questions about our documentation or suggestions for how we can improve it? Start a discussion in TetraConnect Hub. For access, see Access the TetraConnect Hub.
NOTEFeedback isn't part of the official TetraScience product documentation. TetraScience doesn't warrant or make any guarantees about the feedback provided, including its accuracy, relevance, or reliability. All feedback is subject to the terms set forth in the TetraConnect Hub Community Guidelines.
Updated 6 months ago
