AWS WAF Exceptions
Customers hosting the Tetra Data Platform (TDP) in their own environment have the option to add an AWS WAF (Web Application Firewall) component in front of the public-facing Application Load Balancer (ALB). This is an optional security enhancement and requires specific rule group exceptions to allow seamless operation of the TDP's APIs.
AWS WAF helps protect web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. The service provides control over what traffic to allow or block to your web applications by defining customizable web security rules.
Architecture
NOTEA WAF should be used in front of the external ALB, which serves the TDP's API to your users. It is not necessary and may cause issues with internal traffic if deployed in front of the internal ALB.
The following diagram shows an example TDP networking setup that uses AWS WAF:
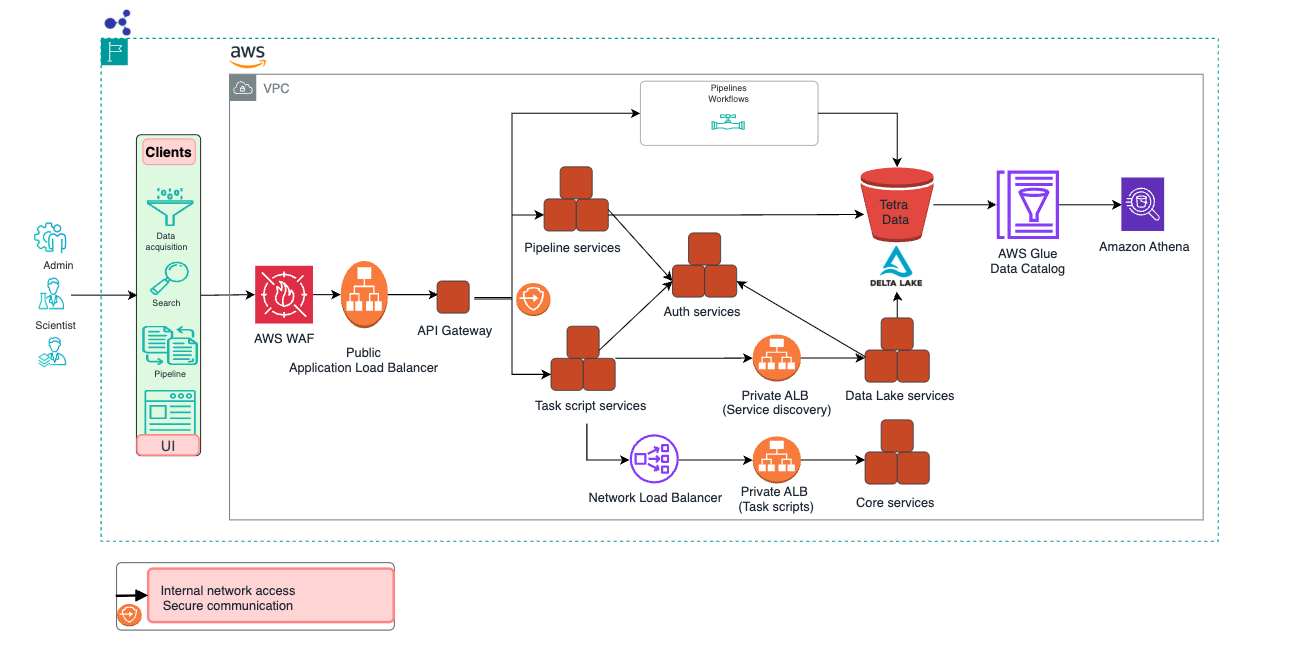
Required WAF Rule Exceptions
To use AWS WAF with the TDP, the following AWS WAF rule exceptions are required:
GenericRFI_BODY Exception
GenericRFI_BODY ExceptionRule Name: GenericRFI_BODY
Rule Group: AWS Core Rule Set (CRS)
Description: This rule inspects the request body for attempts to exploit Remote File Inclusion (RFI) in web applications by embedding URLs that contain IPv4 addresses.
Required Endpoints
- Endpoint:
/v1/commands - Reason: Command payloads legitimately contain URLs as part of their normal operation. Without this exception, valid command requests would be blocked.
SizeRestrictions_BODY Exception
SizeRestrictions_BODY ExceptionRule Name: SizeRestrictions_BODY
Rule Group: AWS Core Rule Set (CRS)
Description: This rule inspects for request bodies that are over 8 KB (8,192 bytes) and blocks them.
Required Endpoints
- Endpoints:
/v1/commands/v1/datalake/upload/v1/datalake/ids-upload/v1/datalake/metadata-tags
- Reason: The Tetra Data Platform supports file uploads of up to 500MB using these endpoints. Without this exception, file uploads larger than 8KB would be blocked.
Implement AWS WAF Rule Exceptions
To implement the required rule exceptions in your AWS WAF configuration, do the following:
- Sign in to the AWS Management Console and open the AWS WAF console at https://console.aws.amazon.com/wafv2/.
- Select your Web ACL.
- Edit the
AWS-AWSManagedRulesCommonRuleSetrule group. - For each rule that needs an exception, do the following:
- Set Override rule action to Count or create a specific rule exclusion.
- Add a rule statement that matches the specific path that needs the exception.
Example Configuration
The following is an example of how to configure AWS WAF rule exceptions by using an AWS CloudFormation template:
Resources:
MyWebACL:
Type: AWS::WAFv2::WebACL
Properties:
# ... other properties ...
Rules:
- Name: AWSManagedRulesCommonRuleSet
Priority: 0
OverrideAction:
None: {}
Statement:
ManagedRuleGroupStatement:
VendorName: AWS
Name: AWSManagedRulesCommonRuleSet
RuleActionOverrides:
- ActionToUse:
Count: {}
Name: GenericRFI_BODY
- ActionToUse:
Count: {}
Name: SizeRestrictions_BODY
ScopeDownStatement:
NotStatement:
Statement:
OrStatement:
Statements:
- ByteMatchStatement:
FieldToMatch:
UriPath: {}
PositionalConstraint: STARTS_WITH
SearchString: /v1/commands
TextTransformations:
- Priority: 0
Type: NONE
- ByteMatchStatement:
FieldToMatch:
UriPath: {}
PositionalConstraint: STARTS_WITH
SearchString: /v1/datalake/upload
TextTransformations:
- Priority: 0
Type: NONE
- ByteMatchStatement:
FieldToMatch:
UriPath: {}
PositionalConstraint: STARTS_WITH
SearchString: /v1/datalake/ids-upload
TextTransformations:
- Priority: 0
Type: NONE
- ByteMatchStatement:
FieldToMatch:
UriPath: {}
PositionalConstraint: STARTS_WITH
SearchString: /v1/datalake/metadata-tags
TextTransformations:
- Priority: 0
Type: NONEResources
For more information about AWS WAF and managed rule groups, see the following resources in the AWS documentation:
Documentation Feedback
Do you have questions about our documentation or suggestions for how we can improve it? Start a discussion in TetraConnect Hub. For access, see Access the TetraConnect Hub.
NOTEFeedback isn't part of the official TetraScience product documentation. TetraScience doesn't warrant or make any guarantees about the feedback provided, including its accuracy, relevance, or reliability. All feedback is subject to the terms set forth in the TetraConnect Hub Community Guidelines.
Updated 6 months ago
